Risk Management Report for SMB Cybersecurity Leaders 2023

Nic Boerma
Small and mid-sized businesses face unique threats in today’s threat landscape. These organisations don’t command the same resources as large enterprises, yet they must respond to many of the same kinds of cyberattacks.
These attacks increasingly use a sophisticated combination of social engineering, credential compromise, and technical exploits to infiltrate target networks. Organisations with less than 1000 employees often have limited options for protecting themselves in a reliable, cost-effective way.
View this white paper to identify how different leaders and types of organisations are responding to ongoing risk management trends.
#RiskManagement #Ransomware #BlackFog #CyberPrevention
7 Ways NetTrace Asset Management Boosts Your Bottom Line
7 Ways NetTrace Asset Management Boosts Your Bottom Line
As businesses evolve, so do their needs, and we’re excited to share with you how NetTrace Asset Management services can be a game-changer for your organisation, enabling significant cost savings through meticulous asset oversight.
- Prevent Costly Problems with Real-time Asset Visibility:
By having a comprehensive view of the location, condition, and custodian of your assets, you can proactively avoid expensive issues, such as duplicate purchases, last-minute maintenance needs, and instances of misplaced assets.
- Enhance Accountability and Efficiency Anytime, Anywhere:
Provide your team with 24/7 access to detailed asset data, fostering accountability and efficiency. NetTrace ensures that employees can track valuable company assets regardless of their physical location, streamlining the workflow and improving overall productivity.
- Optimise Planning and Organisation:
Efficient asset management facilitates better planning and organization within your company. This not only makes employees more accountable but also enhances overall workflow and productivity, reducing losses in the event of natural disasters and curbing employee theft.
- Boost Check-in/Check-out Process:
NetTrace simplifies the check-in/check-out process, making it easier to hold employees accountable for asset usage. This reduces the likelihood of assets being misplaced or not returned on time, contributing to a more streamlined workflow.
- Identify and Mitigate Risks:
Track assets over their entire lifecycle to identify potential risks, such as underperformance, non-usage, or frequent breakdowns. This enables informed financial decisions on whether an asset is beneficial or detrimental to your organisation.
- Eliminate Spreadsheet Hassles:
Move beyond the limitations of spreadsheets and legacy software. NetTrace ensures data integrity through seamless integrations, highlighting data discrepancies, and providing a secure platform for asset management, preventing compromises and errors.
- Streamline Audits and Enhance Data Accuracy:
NetTrace’s NAMSCAN App enables regular in-house audits, ensuring accurate and up-to-date data for your Fixed Asset Register. This streamlines audit processes, reduces manual intervention, and prevents re-audits, saving both time and resources.
NetTrace Asset Management offers a comprehensive solution that not only saves you money but also enhances efficiency and accountability across your organisation.
Make informed decisions, eliminate unnecessary expenses, and streamline your asset management processes with NetTrace.
Contact us at cloudsales@mustek.co.za for to schedule a product discussion and demo.
How to pick the best endpoint detection and response solution for your business.
How to pick the best endpoint detection and response solution for your business.
Endpoint detection and response (EDR) solutions proactively and automatically block and isolate malware while equipping security teams with the right tools to confidently deal with these challenges. A modern EDR can ensure business continuity by effectively mitigating fast-growing, automated and advanced threats, such as ransomware or fileless attacks, without increasing analyst workloads or requiring highly skilled security specialists.
Buyers should look for an EDR that can run autonomously and offer automated detection and response capabilities. This provides analysts with a clear, real-time overview of an attack as it evolves, and can offer guided remediation to quickly return to normal.
Download this buyer’s guide to learn more or simply contact cloudsales@mustek.co.za and our team will be happy to assist you make the right decision.
#Cybersecurity #ThreatDetection #EDR #EndpointSecurity #CyberProtection
Empower Your Mobile Workforce - Samsung Knox
Whether you're a small business or a large enterprise, Samsung Knox is here to empower your mobile workforce, protect your sensitive information, and drive efficiency.
With Knox, you get:
• Robust Security: Fortify your devices against threats with multi-layered security measures. Your data is safe, no matter where it goes.
• Device Management: Easily manage and configure your fleet of devices, ensuring seamless functionality and compliance.
• Enhanced Productivity: Boost your team's productivity with a secure workspace for business apps, while keeping personal data separate.
• Seamless Integration: Knox integrates with a wide range of Enterprise Mobility Management (EMM) solutions and supports various platforms.
Discover how Samsung Knox can transform your mobile security and management strategy. Contact us on cloudsales@mustek.co.za and let's discuss this innovative solution.
#SamsungKnox #MobileSecurity #EnterpriseMobility #Innovation #Productivity #CyberSecurity
Mustek to Expand Security Portfolio with a partnership with IBM Security - ReaQta
Mustek to Expand Security Portfolio with a partnership with IBM Security – ReaQta
About IBM Security and ReaQta
Mustek Limited’s Cloudshop has announced its partnership with IBM’s ReaQta Division. This is an expansion of its cybersecurity threat detection and response capabilities with the introduction of ReaQta. IBM ‘s ReaQta’s endpoint security solutions are designed to leverage AI to automatically identify and manage threats, while remaining undetectable to adversaries. This move will expand Mustek’s capabilities in the extended detection and response market, to deliver security with an open approach that extends across disparate tools, data, and hybrid cloud environments. “Complexity has created a cloak that attackers are operating under, furthering their ability to circumvent defenders,” said JP Gough, Executive of Cloud, Software, and Solutions at Mustek. “The future of security is open, using technologies that can connect the security insights that are buried across disparate tools and advanced AI to identify and eliminate threats faster than ever before.”
Mustek and IBM Security have come together to provide a unified security platform that enables the integration of data from multiple sources. This will allow customers to detect and respond to threats faster, no matter where they occur. The combined platform will also allow customers to quickly address security issues across hybrid cloud environments and protect against advanced threats.
IBM’s acquisition of ReaQta further differentiates the company’s portfolio of connected, open security tools to unify and speed response to security threats. ReaQta, whose primary business office is in the Netherlands with headquarters in Singapore, has joined the IBM Security business unit. ReaQta was built by an elite group of cybersecurity experts and researchers with AI and machine learning expertise and extensive backgrounds in security operations.
ReaQta’s behavioural-based platform helps stop known and unknown threats in real-time and can be deployed in a hybrid model – on premise or in the cloud as well as air gapped environments. Through deep learning done natively on the endpoint the platform constantly improves on defining threat behaviour tailored to each business per endpoint, allowing it to block any abnormal behaviour. ReaQta’s platform also leverages a unique ‘Nano OS’ that monitors the operating systems from the outside, helping to prevent interference by adversaries.
“Our mission at ReaQta has been to better equip the defenders, who are tirelessly striving to stay ahead of cyber threats, with advanced technology to quickly identify and block new attacks,” said Daan Haaker, EMEA Sales lead at ReaQta. “Joining forces with Mustek will help us expand across South Africa. With this ecosystem that we are building in South Africa, Mustek Limited fits perfectly. We are looking forward to seeing our partnership grow and flourish across the region.
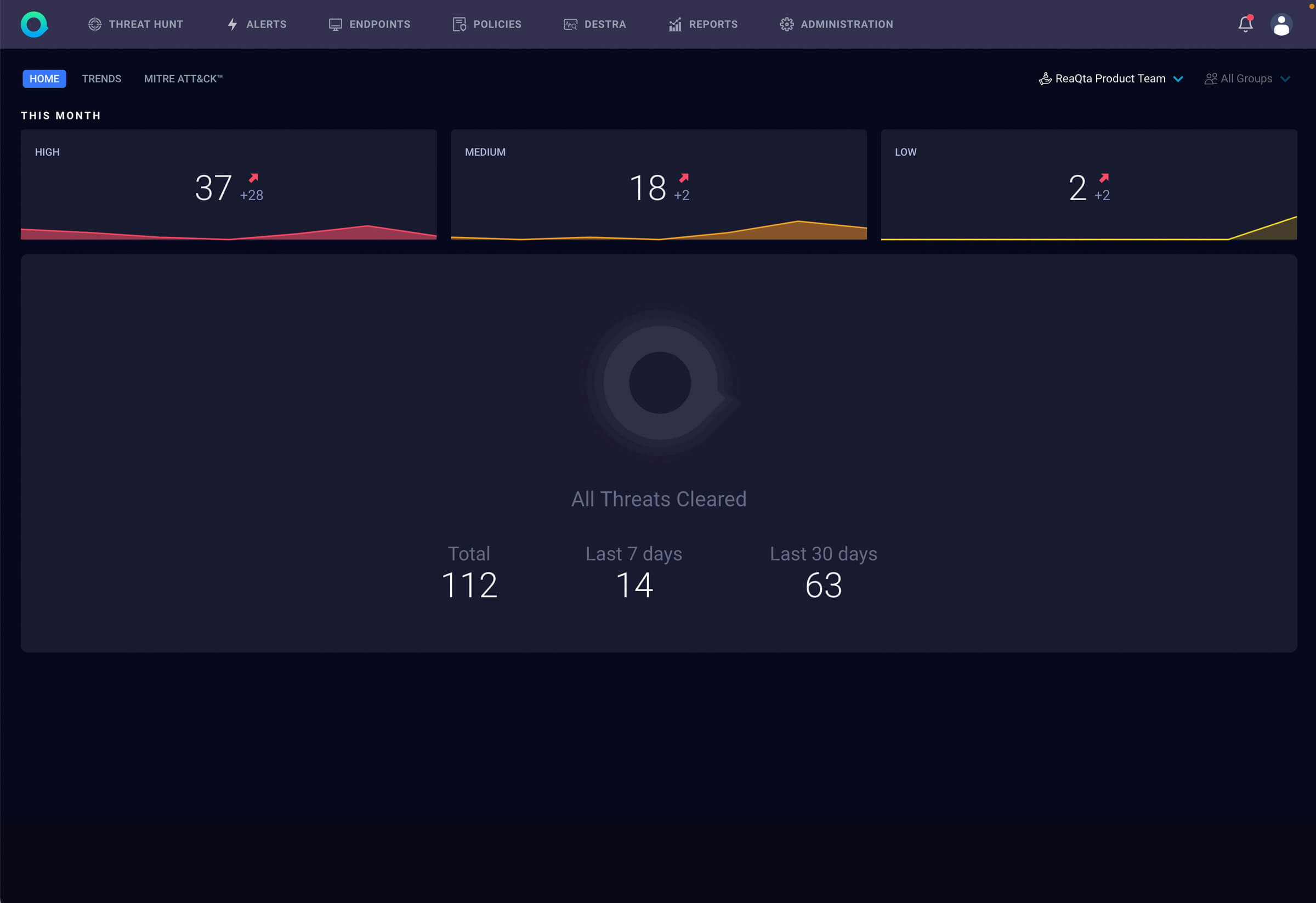
Mustek MDR Security Solution
In collaboration with IBM’s ReaQta, Mustek’s Cloudshop has developed a Managed Detection and Response Solution which delivers a 24/7 threat detection and quick response capability. Mustek’s Cloudshop MDR services uses advanced threat detection techniques, such as behavioural analysis, machine learning, and artificial intelligence to detect and respond to sophisticated threats. This MDR technology also leverages threat intelligence feeds and security research to stay up to date on the latest threats and attack techniques, ensuring that one’s business is protected against emerging threats. When integrated with our Security Operations Centre (SOC) partner, the endpoint detection and response (EDR) data can be correlated with other security data sources to provide comprehensive threat intelligence. EDR integration into the SOC allows us to identify gaps in security infrastructure and recommend improvements. By combining this MDR solution with our SOC partner, one can benefit from the 24/7 monitoring and response of an experienced team, as well as deep understanding of the threats facing your organization. Our team of security experts will provide detailed analysis, threat prevention, and the latest threat intelligence to ensure that any detected incidents are quickly identified and responded to. Furthermore, our partner’s security analysts are trained.
Mustek reseller’s, will have the opportunity to white label our MDR solution and sell it on as their own solution.
About IBM Security and ReaQta
IBM Security offers one of the most advanced and integrated portfolios of enterprise security products and services. The portfolio, supported by world-renowned IBM Security X-Force® research, enables organizations to effectively manage risk and defend against emerging threats. IBM operates one of the world’s broadest security research, development, and delivery organizations, monitors 150 billion+ security events per day in more than 130 countries, and has been granted more than 10,000 security patents worldwide. ReaQta is a top-tiered AI Autonomous Detection & Response platform, built by an elite group of cyber security experts and AI/ML researchers. Built with advanced automated threat-hunting features, ReaQta allows organizations to eliminate the most advanced threats in real-time. As experts in AI and behavioral analysis, ReaQta’s proprietary dual-AI engines provide organizations across all industries with autonomous, real-time, and fully customizable endpoint security, minus the complexity. As a result of automation coupled with intuitive design, ReaQta’s customers and partners benefit from performance improvements and are now able to manage and secure more endpoints without the need for highly skilled staff.
About Mustek
Mustek is one of the largest assemblers and distributors of personal computers and complementary IT products in South Africa. Mustek is the operational business division of the Mustek Limited Group (established in 1987) which also includes Rectron. By combining the best of local assembly capabilities of the Mecer brand with a multinational product portfolio via a broad range of top tier ICT brands, Mustek is focused on being the country’s ICT supplier of choice. Through the supply of configuration and customisation, tried and trusted best industry practices, and competitive pricing, Mustek is positioned to service a wide range of technology needs. For more information about Mustek and its proven track record of solution formulation and superior technical expertise, visit www.mustek.co.za.
Acronis Advanced Management
When something goes wrong with your IT, everything grinds to a halt. What if you could keep your IT from breaking in the first place, be proactive rather than reactive, or fix issues ahead of time, before the point there is a problem?
With a huge reduction in those crisis moments, your employee productivity will increase and become more predictable. A proactive approach takes the complexity out of technology by providing comprehensive support — with no surprises.
WannaCry. Equifax. Notpetya. These three most dangerous and well-known #cyberattacks all have one thing in common: They were caused by companies leaving their systems unpatched for extended periods of time. Unpatched systems are one of the easiest attack vectors for cybercriminals looking to gain access to corporate networks and systems.
Download this Acronis Advanced Management Data Sheet and see what Acronis can do for you.
#cybersecurity #advancedmanagement #patchmanagement
Asus and Acronis Cyber Protect Bundle

Nic Boerma
Acronis Cyber Protect Home Office
The #1 Integrated Backup and security in one solution.
For your home and small office data on Windows, macOS, Android, and iOS
- Complete backup and fast recovery – Quickly restore your files or entire system at any time
- Easy disk cloning and full image backup – Just two clicks to start a full disk image backup
- Cloud, local or hybrid cloud backup – Back up locally, to the cloud, or both. It’s your choice
- Integrated backup, antivirus and anti-malware protection – Keep cyberthreats away from your device and backup data
Learn more about Acronis Cyber Protect Home Office here.
What’s in it for you?
The Acronis cards will be attached to your Asus order at no additional cost. By participating in this promotion, you can claim a 10% rebate from MSRP for every Acronis license activation. Activations occur when the Acronis card’s unique redemption code is redeemed through the Sundae website.
There is also a share feature to the redemption process, one code can be redeemed more than once. So, if your customer shares with three people and they all redeem, you’ll get your 10% rebate three times.
| SKU | Storage | # of devices | Sundae retail price ex.VAT | Your price ex.VAT | Rebate value |
|---|---|---|---|---|---|
| Acronis Cyber Protect Home Office | 50GB | 1 Computer | R330.43 | R297.39 | R33.04 |
| Acronis Cyber Protect Home Office | 50GB | 3 Computers | R513.04 | R461.74 | R51.30 |
| Acronis Cyber Protect Home Office | 50GB | 5 Computers | R634.78 | R571.30 | R63.48 |
Customer Redemption Process
Your customers can redeem their codes and receive their discounted software through six simple steps:
- Lift and open the tab on the card to reveal the URL and redemption code
- Enter the url into a browser or scan the QR code. Enter the redemption code once the webpage loads
- View and select the offer most suited
- Enter user details in the necessary fields
- Pay via Paygate, a secure payment gateway
- Follow the download link displayed (and emailed) to install the Acronis software
Data Breach Prevention

Nic Boerma
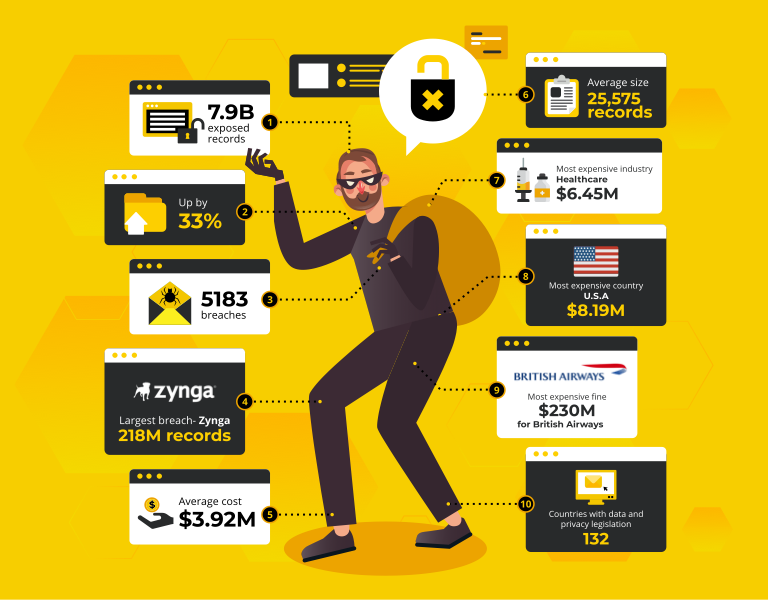
Despite increased global legislation around data protection, and a heightened consumer awareness around privacy and misuse of data, breaches were up a staggering 33% up on last year. Hardly a week goes by without a major data breach hitting the headlines, with some of the largest global corporations being named and shamed.
Download this e-book: YOUR LINK and learn about the cold truth about cybersecurity in the 21st century.
With data breaches on the rise, it’s time to put serious focus onto anti data exfiltration.