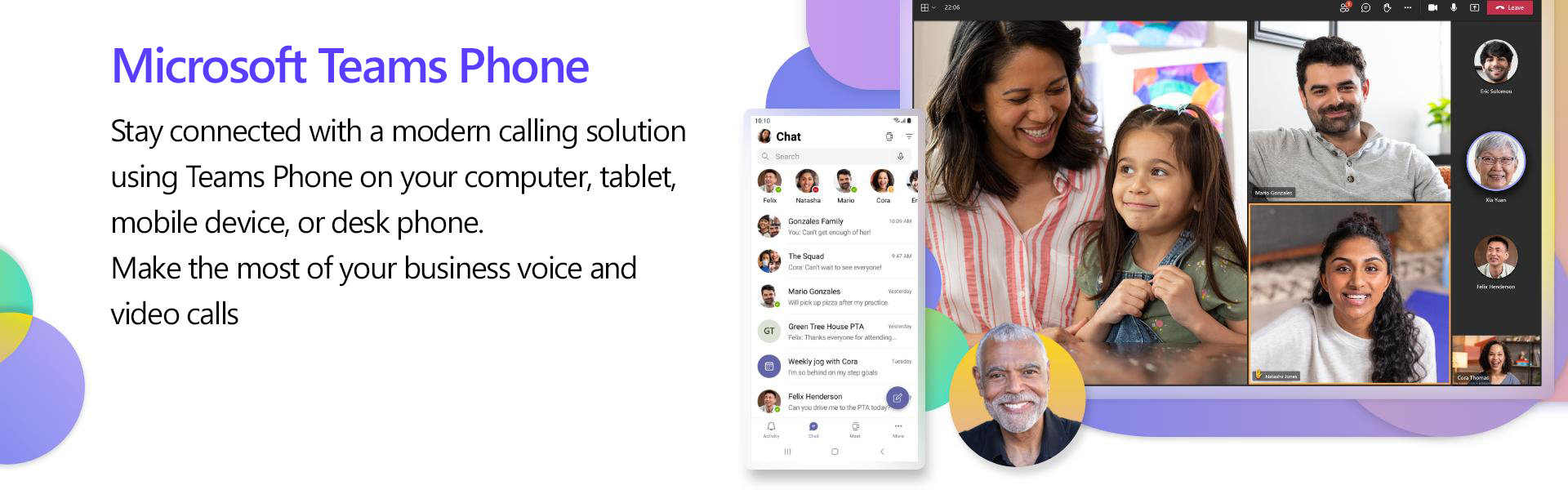
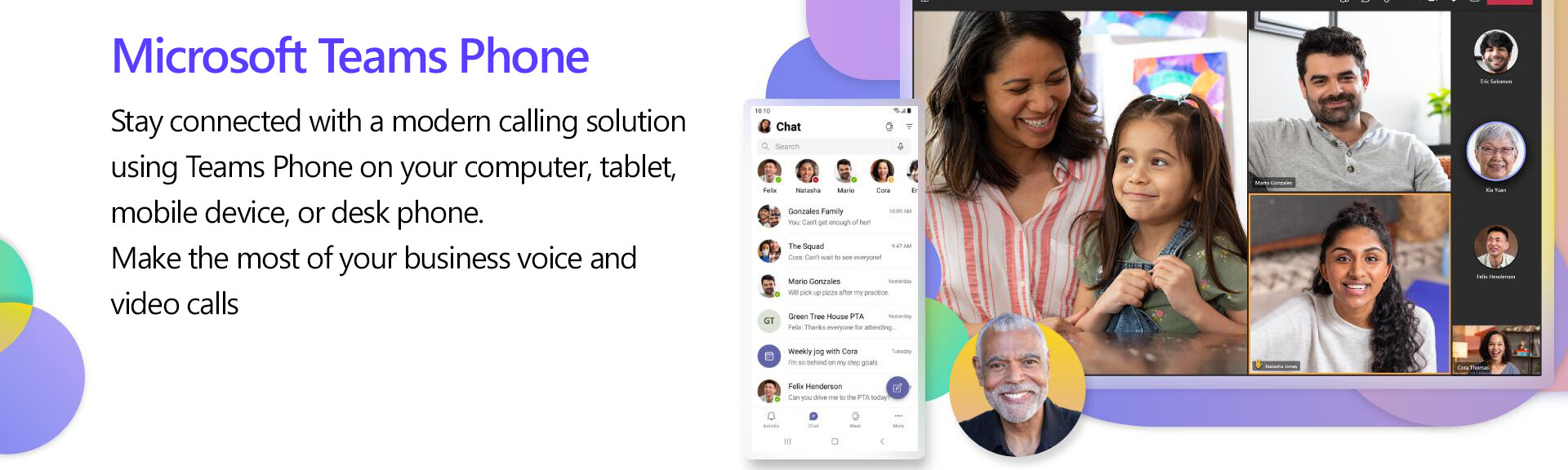
Stay connected with voice and video calling using Teams Phone on your computer, tablet, mobile device, or desk phone.
Mustek
Microsoft Teams Phone is a Cloud-based phone system with advanced features including call transfer, multilevel auto attendants, and call queues.
Make the most of your business voice and video calls.
Microsoft Teams Phone FAQ
What is Microsoft Teams Phone?
Teams Phone refers to the capability of people to make and receive calls in Microsoft Teams. Teams subscriptions include Teams Phone and enables calls from one Teams app to another. Making and receiving calls to and from landlines and mobile phones on the public switch telephone network (PSTN) in Teams is available with an add-on such as Teams Phone Standard or Teams Phone with Calling Plan or is included in Microsoft 365 E5. These options provide a cloud-based phone system in Teams with features such as hold, blind and safe transfers, and reporting features for professionals who manage calling solutions.
How does Teams Phone system work?
It replaces traditional PBXs and enables key calling capabilities with a cloud-based call control system that provides the overall telephony workload for Microsoft Teams.
What is a Microsoft Teams calling plan?
A calling plan provides customers with a primary phone number and calling minutes to make and receive phone calls. A domestic calling plan is included in Teams Phone with Calling Plan or can be added onto Microsoft 365 E5.
What is Direct Routing?
Direct Routing helps you connect a supported, customer-provided SBC to Phone System. With this capability, configure on-premises PSTN connectivity with Microsoft Teams client.
What is Operator Connect?
Direct Routing helps you connect a supported, customer-provided SBC to Phone System. With this capability, configure on-premises PSTN connectivity with Microsoft Teams client.
Can I use my existing phone numbers?
Yes. You can transfer your phone numbers from your current service provider. After you port your phone numbers over, Microsoft will become your service provider.
Can I bring my own calling plan?
Yes, customers can work with their Microsoft partner to bring their own calling plan. A configuration called Direct Routing allows customers to connect voice trunks directly from their network to Teams or interconnect other telephony entities, such as call centres or analogue devices.
Microsoft Teams Phone Standard is a standalone subscription (without a calling plan) that is specifically designed for this situation.
What phones are supported?
Devices certified for Teams provide a seamless Teams experience on desk phones, conference phones, and meeting room systems. Learn more about Microsoft Teams-certified devices. For available devices go to the Microsoft Teams Devices Marketplace.
Teams supports a portfolio of desk phones for customers who require a traditional phone experience.
To deliver a high-quality and reliable Teams experience on phones, Microsoft is partnering and actively working with Yealink, Crestron, Lenovo, Polycom, and Audio-codes to develop and certify a wide portfolio of desk phones and conference room audio devices. To get the latest information on Teams devices, go to Teams Marketplace.
What is the difference between the offers for small and medium-sized business and enterprises?
There are two offers for small and medium-sized businesses. Teams Phone with Calling Plan combines a phone system and a domestic calling plan.
Teams Phone Standard without a calling plan provides a phone system which requires a calling plan from a service provider.
For enterprises: A phone system and audio conferencing are included in Office 365 E5 and Microsoft 365 E5. A Teams calling plan can be added on or can all be purchased separately. Enterprises can also add Teams Phone with Calling Plan as an add on to qualifying subscriptions.
Teams Phone with Calling Plan is currently available in 31 markets. See country and region availability. A phone system is available in over 120 countries, everywhere Microsoft 365 is available.
The product features and experience are the same across the offers for small and medium-sized businesses and enterprises. Pricing and availability may differ.
What is Microsoft Teams essentials and Azure AD Identity?
Microsoft Teams Essentials with Azure AD Identity brings together the best of Teams with meetings, chat, calling, and collaboration. Teams Essentials with Azure AD Identity can connect to your existing email system to provide an integrated experience, such as having all Teams notifications sent to your existing email inbox, all calendar events in Teams, and the ability to sign into Teams with your existing email address. Once connected, you’ll see responses to scheduled meetings and collaboration invitations in both your inbox and in Teams. View and interact with incoming meetings from your Teams calendar, whether your contacts are using third-party meeting software or Teams.
Teams Essentials with Azure AD Identity can be purchased only through select cloud solution provider.
To learn more or to transact contact: Cloudsales@mustek.co.za
The first step in defending against #date #exfilration is to understand exactly what it is and how it works
Mustek
The first step in defending against #date #exfilration is to understand exactly what it is and how it works. We’ve covered everything you need to know about #DataExfiltration and how to prevent it here
Cybersecurity is now the biggest challenge that many businesses face. According to AON, cyberattacks leading to sensitive data breaches and ransomware are now the number one concern for businesses in North America and the UK, ahead of issues such as business interruptions, economic slowdowns and supply chain risks.
The costs of these incidents continue to rise, with figures produced by the Ponemon Institute on behalf of IBM noting that in 2021, the average cost
of a data breach reached $4.24 million – the highest figure in the 17 years it has been conducting this research.
A particular threat that businesses must be aware of is data exfiltration. This can have a wide range of expenses, from reputational damage and lost business, through to ransom payments, class action lawsuits and regulatory penalties. As such, it’s vital that businesses are aware of this threat and are taking the right steps to mitigate it.
What does data exfiltration mean?
The first step in defending against data exfiltration must be to understand exactly what it is and how it works. It is a term used to describe the movement of data OFF a device, as opposed to infiltration, the movement of data ON to the device.
What is data exfiltration?
Data exfiltration is the unauthorised removal of data from a device, which may be an endpoint such as a PC or smartphone or a database server, for example. This form of data security breach can be among the costliest to a business, as it can be extremely hard to spot. Indeed, in many cases, hackers have been able to transfer materials undetected for months, allowing them to build up a huge repository of sensitive data.
How does data exfiltration occur?
There are a few ways in which data exfiltration works, but they essentially come down to two key attack vectors – outsider attacks and insider threats.
Outside attacks often use techniques such as injecting malware or using phishing attacks to steal credentials and gain access to confidential and encrypted data. Once inside, they can copy data and transfer it back to the attackers at will. In some cases, hackers have been found to exfiltrate data for months or even years before being discovered.
Insider threats, meanwhile, originate from a company’s own employees. This may be inadvertently such as users being careless with their data handling, or more intentional. In these cases, a malicious insider may deliberately copy and remove data, which they can then sell on to criminals or deliver to a competitor, for example. In some cases ransomware gangs are actively recruiting insiders https://www.bleepingcomputer.com/news/security/lockbit-ransomware-recruiting-insiders-to-breach-corporate-networks/ to help them breach corporate networks and execute successful attacks.
Why does data exfiltration occur?
For cybercriminals, exfiltrated data is a highly valuable resource. For instance, sensitive information such as personal customer data or corporate financial details can be used directly to commit fraud or sell on to other criminals. However, other confidential information such as trade secrets or other proprietary information may also be of use as part of corporate or even state-level espionage. In fact, a new service known as Industrial Spy , which promotes itself as a marketplace where businesses can purchase their competitors’ data, has recently been set up by threat actors.
Another growing problem is the risk of cyber extortion, where hackers threaten to publicly release private data online. This is often part of a ransomware attack and can also be highly lucrative, as many firms may feel paying up will be cheaper in the long run than dealing with the repercussions of public data exposure. In 2020, research by RUSI found there were 1,200 so-called double extortion ransomware incidents, with over 60% of these aimed at the US and the UK.
What are the implications of data exfiltration?
Falling victim to a data exfiltration incident can have numerous consequences, both financially and reputationally.
Where is the majority of exfiltrated data going?
Hackers are constantly becoming more organised, with criminal gangs increasingly recognising the value of stolen data, both as a resource they can use directly for activities such as ransomware extortion and to sell on easy profit.
BlackFog’s own research indicates that almost a fifth of exfiltrated data (19 percent) ends up in Russia. The dark web is another popular destination for stolen data, where it can be freely shared and traded. In 2022, for example, confidential data on unreleased iMac products were briefly published online by hacking group REvil after Apple refused to pay a $50 million ransomware demand.
Can exfiltrated data hurt your business?
Stolen data can be harmful to a business in a number of ways. Primarily, it can lead to unhappy customers and lost business, as well as the attention of regulators. With tough legislation threatening heavy fines for businesses that fail to protect sensitive data – up to $20 million or four percent of global revenue under GDPR, for example – the financial cost can be high.
Firms that hold extremely sensitive proprietary data or trade secrets could also lose any competitive advantage they have in the market by giving away designs or future development plans to rivals.
All this is before you consider the reputational damage that a data privacy failure can lead to. With consumers more sensitive than ever to misuse of personal information, they will rarely be quick to forgive a company that has proven unable to take care of their data. For instance, McKinsey notes that 87 percent of people will not deal with a firm if they have concerns about its security practices, while 71 percent said they would stop doing business with a company that gave away sensitive data.
What are the long-term costs of data exfiltration?
In the longer term, companies that have fallen victim to data exfiltration can find themselves facing a range of costs. In addition to regulatory penalties, the threat of class-action lawsuits from affected customers can be high.
As well as direct compensation, preventative measures such as credit monitoring services for any users who had financial details stolen can be a major expense. Elsewhere, the reputational damage such incidents can inflict is also huge and is something smaller companies may never recover from. Indeed, it’s claimed that as many as 60 percent of small businesses close within six months of a data breach.
How to prevent data exfiltration
The best defence against data theft is to block it before it happens. Once data has been extracted from a network, the damage is already done, so mitigation and incident response plans can only have a limited impact. You therefore need an anti-data exfiltration, or ADX, solution that stops your business from falling victim in the first place.
How can data exfiltration be prevented?
A key part of any ADX strategy is to monitor all traffic that is leaving the business’ network. Many traditional cybersecurity solutions focus their efforts on protecting the network perimeter against incoming threats.
While this remains an important layer in your cybersecurity defence strategy, relying solely on perimeter defence tactics will leave you vulnerable should something slip through the net – which, given the prevalence of risks such as zero-day threats, is likely to happen to every business sooner or later.
Therefore, you need to go beyond standard cybersecurity techniques, including data loss prevention (DLP) tools, and look for solutions designed specifically to stop attackers from exfiltrating unauthorised data. This helps you take control of how information flows through your network and ensure that when it is transferred beyond your borders, it is fully authorised and secured.
How can you protect from data loss by negligent, compromised and malicious users?
People who are careless with their credentials – either through weak protections or sharing of details – are among the main causes of data exfiltration. In fact, the Ponemon Institute claims this is the most common root cause of attacks, accounting for 20 percent of all breaches in 2021.
Putting controls in place to prevent reckless behaviour such as password sharing or accessing data via unsecured devices and network connections is a must. However, to be effective, you need to go further to also counter any malicious actor within your business who may be looking to steal data.
To do this, strong ADX solutions must include effective monitoring tools that can keep a close watch on data leaving the network. Using behavioural profiling techniques, suspicious activities – such as users attempting to access resources they do not have permission for or transferring files in an usual way – will be blocked, ensuring that unauthorized data doesn’t leave the network.
The importance of endpoint protection for data exfiltration prevention
Focusing on your endpoint security is another essential part of preventing a data exfiltration attack, and this is something that’s particularly important in the new era of remote and hybrid working, where more business activities take place on personally owned and mobile devices that can often be overlooked by a traditional DLP solution.
For instance, in 2020 – when remote working became the norm for many people – ransomware attacks spiked by 150 percent compared with the previous year. This is no coincidence, as many attackers looked to take advantage of less direct oversight. As these trends are here to stay for many enterprises, on-device security solutions ensure that your threat detection tools extend to every part of your network, no matter where they are or who they belong to.
How does BlackFog prevent data exfiltration?
Unlike many other data protection tools, BlackFog uses a layered approach that can identify in real-time any data exfiltration attempts and shut them down before they have a chance to succeed. Our ADX technology provides full on-device protection by blocking outbound data transfer activities to disrupt cyberattacks and protect sensitive data.
With a complete endpoint protection platform to guard against data loss, BlackFog’s unique ADX solution helps block any possible avenue for attackers to conduct a data exfiltration attempt, whether this originates from a hacking attempt, phishing attacks or an insider threat.
Browse our range of products to find out more about how BlackFog ADX can help keep your business safe from the latest threats posed by cybercriminals.
BlackFog is proudly distributed by Cloudshop by Mustek, Mustek’s Cloud and Software division.
To learn more or to transact contact: cloudsales@mustek.co.za
Stop email cyberthreats with Advanced Email Security - Acronis

Mustek
Advanced Email Security is an API-based email security technology that integrates directly into the email system without the need for any additional configuration, including configuring MX records. If you already use Acronis Cyber Protect Cloud, implementing Advanced Email Security happens with the flip of a switch.
Leading Acronis experts will show case how to use this technology keeping your email system up and running and free from threats.
To learn more about Acronis Cyber security technologies or to start transacting contact Cloudsales@mustek.co.za +27 11 237 1000
How to back up Microsoft 365 Email Backup on Acronis

Mustek
With Acronis Backup Cloud’s support for Office 365 email, you can offer your customers a valuable backup service to protect all of their email data while also complementing your Office 365 sales. Using the brandable, self-service Acronis Backup Cloud console, your customers can control their backups, centrally view all activities, and receive problem alerts for all their protected data — including Office 365 email.
Service provider benefits:
Generate additional monthly recurring revenue with competitive pricing and attractive margins.
Realize incremental revenues by offering expanded data protection services for your customers’ entire environment.
Add value to every Office 365 sale by protecting your customers’ mailboxes with fast, efficient backup.
Eliminate operational overhead and streamline backup sales via integration with Odin Service Automation.
Ensure compliance by meeting data protection regulatory requirements and providing robust search and recovery.
Offer your customers the flexibility to back up their data locally or to private or public clouds.
Reduce complexity with a unified web-based data protection console.
This Cloudcast will help you understand why you should back up your 365 email on Acronis and will take you through the how to do it.
Should You Pay a Ransomware Demand?

Mustek
To pay or not to pay? With over a third of all companies facing this dilemma last year alone we take a look at the pros and cons of paying the #ransom in our latest blog : #ADX #DataExfiltration #Cybersecurity
Should You Pay a Ransomware Demand?
What are the Pros and Cons?
Receiving a ransomware demand is something every business dreads. It is no longer a matter of if you will get attacked, but when. Ransomware struck one -third of all organisations in 2021 alone. It’s something that every security team will have to deal with.
What’s more, once-standard mitigations such as reverting to backups may no longer be enough to recover data if critical files have been encrypted. Many ransomware demands now threaten to release data publicly if the ransomware demand is not made in a timely manner. Many also release samples to prove they have the data as many victims naively think it’s a bluff or feel they have adequate protections in place.
Other threats may include exposing firms to the threat of regulatory action or initiating DDoS attacks to further disrupt operations. And with the clock ticking, firms have to make quick decisions about whether to pay the ransom to avoid further consequences or brace themselves for the fallout.
The Benefits of Paying a Ransom
Many firms may decide that the easiest way to restore services and remain operational is to simply pay the ransom. As long as everything goes to plan, this can minimize disruption and downtime, as well as avoid significant financial losses beyond the ransom itself.
Some firms may also believe this will help them keep the incident quiet and avoid any adverse publicity – although regulatory reporting requirements may still apply depending on the sector they operate in and the information compromised.
For organizations in critical sectors such as healthcare, utilities or infrastructure, remaining operational may be such an important consideration that paying the ransom is the only viable option.
Disadvantages of Giving in to Ransomware Demands
One of the biggest issues with paying a ransom is that you’re gambling that hacker will keep to their word and restore systems. Unfortunately, when you’re dealing with criminals, there’s no guarantee. In fact, it’s estimated that as many as 92 precent of firms fail to recover all of their data, with nearly a third losing at least half.
If the hackers have successfully exfiltrated data as part of their attack, there’s also no way of knowing what they’ll do with this, even if a ransom is paid. Many cybergangs make additional revenue by selling the data on the dark web, especially if it contains valuable intellectual property or customer data. This can cause significant long term problems for the organization in terms of lost competitiveness and reputational damage.
Finally, perhaps the biggest issue with paying ransomware is that it encourages future attacks. If the attackers know you pay then they often come back two and even three times, making it impossible to get ahead of the attacks.
This isn’t just bad for the cybersecurity sector as a whole – it also paints a big target on individual businesses. Some estimates suggest 80 percent of companies that pay a ransom will fall victim again. Of these, only around half are thought to come from the original hackers, highlighting how quickly weak and profitable targets are disseminated in the cybercriminal network.
The Impact on Ransomware Insurance
Some firms may reason that if they pay the ransom, they will be able to claim this against their cybersecurity insurance policy. However, this often leads to more problems.
Over the last few years, ransomware payments for these incidents have skyrocketed, and ransomware insurance providers have created very strict policies. In order to mitigate their own losses, insurance carriers are tightening up limits on how much they’ll pay and under what circumstances.
Whether or not an insurance policy will pay can depend on a wide range of factors. Some, such as AXA, have stopped paying out for ransomware altogether, while others are making their coverage terms much tighter, for instance, by increasing their requirements for firms to have comprehensive protections in place.
To learn how to protect your organisation from #ADX #DataExfiltration #Cybersecurity by using BlackFog data security and ransomware protection contact Cloudsales@mustek.co.za
Backing up Microsoft 365 data is critical

Mustek
Protect clients’ Microsoft 365 applications and data with comprehensive cyber protection that unifies data protection, cybersecurity, and end point protection management in one.
You can directly back up client data from Microsoft data centers to the highly secure Acronis data center.
Back up for:
- Microsoft Exchange Online
- Microsoft OneDrive for Business
- Microsoft SharePoint Online
- Microsoft Teams
Please click on the video below to learn more about…How:
- To get started
- To onboard
- To attach mailboxes to Acronis for backup
- To upload and attach individual boxes
- To group boxes and specific mail folders.
Swift 3 - Thin Laptop for Students | Acer
Say hello to the all-new 14” pick-up-and-go. Bringing heavyweight performance within a color-washed lightweight shell, so you can make magic whenever, wherever—featuring 12th Gen Intel® Core™ processors optimized for multitasking and a QHD or FHD touch display that is as bright as it is brilliant.
Mustek Solar Roof Project
Mustek in Midrand, Johannesburg, is running one of the biggest solar energy projects in South Africa, saving up to R80,000 in electricity per month. Talk Radio 702's Aki Anastasiou visited Mustek to find out more.
Data Exfiltration 101: How Threat Actors Compromise Networks

Mustek
Cybercriminals use a wide variety of attack vectors to infiltrate corporate networks. From that point, they may spend weeks or months conducting research, identifying vulnerabilities, and exfiltrating sensitive data to their own servers for data theft extortion. Data exfiltration 101 describes the types of attacks that lead to data exfiltration and why 83% of all attacks rely on it as the primary vector.
There are many kinds of attack vectors. They include everything from malicious email attachments to insider threats and sophisticated technical exploits.
Cybersecurity professionals and IT leaders must constantly allocate resources to detect and prevent attacks on these vectors. Knowing which ones cybercriminals are currently focusing on helps security leaders make efficient use of those resources.
This information is obviously important for detection since detection-based systems tend to narrowly target certain vectors. It’s also important for prevention-based cybersecurity because it informs IT leaders’ greater security strategy. If you don’t know where attacks are coming from, preventing them is a near-impossible challenge.
Global Statistics: Today’s Most Targeted Sectors
Cybercrime trends change based on the specific sectors and industries targeted. According to BlackFog’s 2021 Annual Ransomware report, the most frequently targeted sectors of 2021 were:
- Technology – 89% increase year-over-year.
- Healthcare – up 30% year-over-year.
- Retail – up 100% year-over-year.
- Government – up 24% year-over-year.
Considering the economic and geopolitical upheaval taking place in Eastern Europe as a result of Russia’s invasion of Ukraine, it’s likely that many of these sectors will see themselves targeted even more in the near future. Government and military agencies in particular are likely to experience concentrated attack efforts made by state-supported cybercriminal organizations.
Your own organization’s risk profile depends on whether it is an enterprise-level organization or a small to mid-size business. Cybercriminals modify their tactics, techniques, and procedures based on the size and preparedness of their victims.
Top 5 Enterprise Attack Vectors
Large enterprises can typically afford to implement a complex set of cybersecurity tools, with. 80% using between 3 and 19 different cybersecurity tools. Many of these tools are industry-leading security platforms operated by highly experienced security personnel.
However, cybercriminals have learned to exploit vulnerabilities in highly complex enterprise security environments. They may focus their efforts on incompatibilities between different enterprise tools or compromise trusted accounts and try to hijack those tools for their own use.
Some of the most common attack vectors today’s enterprises face include:
Fileless Malware Attacks
Fileless attacks rely entirely on the exploited system’s memory, running without requiring installation. Fileless malware often consists of malicious code injected into running processes like JavaScript, which makes it incredibly difficult to detect by conventional means.
Phishing and Spear Phishing
Phishing attacks remain one of the most common entry points cybercriminals use to defraud enterprise users. Email remains the most popular format, with special attention to high-value email accounts that receive large volumes of incoming mail.
Potentially Unwanted Programs
It’s common for enterprise employees to unknowingly consent to downloading programs and files alongside legitimate applications. In the past, these applications typically included spyware and adware. Now, cybercriminals are using them to install keyloggers and gain access to privileged user accounts.
Brute Force Password Attacks
While most enterprises have strict password policies, many employees fail to adhere to them. Many organizations still require employees to set eight-character passwords even though attackers can now crack these codes in less than one hour.
Outdated Software on Endpoint and Special-Purpose Devices
Endpoint systems and special-purpose devices running on legacy software are easy targets for hackers. Special-purpose devices can include POS terminals, check-in kiosks, and smart appliances of any kind. Industrial enterprises have additional vectors in their rapidly expanding fleets of Internet-of-Things devices.
Enterprises can improve their security posture by consolidating their security solutions and reducing the complexity of their tech stacks. Overly complex security environments contain many moving parts that highly motivated cybercriminals may successfully bypass.
Small and Mid-Sized Businesses are Particularly Vulnerable
Cybercriminals have learned to target smaller organizations instead of large, well-defended enterprises. They now target smaller businesses that are often unable to adequately defend themselves the way large enterprises can.
More than 80% of smaller organizations have less than 10 cybersecurity tools deployed. One third of these have only one or two tools at their disposal.
Over 40% of cyberattacks target small businesses. Attackers now use highly automated workflows to identify vulnerable organizations and launch attacks to probe their defenses. The three most common types of attacks on small businesses are:
- Phishing and Social Engineering Attacks: 57%
- Compromised and Stolen Endpoint Devices: 33%
- Credential Theft Attacks: 30%
Small and mid-sized businesses can effectively address security risks by hiring qualified managed security service providers who use best-in-class technology. These services often come at a vastly reduced rate compared to in-house expertise, giving smaller organizations access to enterprise-level technology at favorable cost.
However, small businesses must pay close attention to their security partners and the technologies they use. Competent, reputable partners who use a balanced set of technologies (including both detection and prevention-based solutions) are worth the higher rates they often charge.
Anti Data Exfiltration (ADX)
Today’s cybercriminals can use a variety of methods to gain access to protected networks, and there are signs this trend will increase sharply in the near future. Enterprises and small businesses alike should look beyond detection-based solutions to ensure their most sensitive data is truly secure.
All of the attack vectors listed above share a single factor in common. In order for the attack to succeed, data must travel from inside the protected organization to the outside. Attackers must somehow coordinate with software located inside the target’s network.
Data exfiltration protection serves as a critical layer of protection against ransomware, data breaches and malware attacks. This prevents cybercriminals from accessing sensitive data and cuts off communication between compromised accounts and cybercriminal Command & Control centers.
Small businesses, managed security service providers, and large enterprises alike should make this prevention-based technology a crucial part of their overall security posture. Stop cybercriminals from accessing protected data and protect your most sensitive assets from exploitation.
BlackFog proudly distributed by Mustek
Contact Cloudsales@mustek.co.za or complete the form below to get a sales person to contact you
Error: Contact form not found.
Upselling Microsoft 365 Licenses - a deep dive into different licenses and the benefits.

Mustek
This week’s CloudCast Edition is a Q&A session between Noluthando Shabalala, Mustek’s Cloud and Software division’s Division Product Manager and Ax Xenios, Solutions Architect discuss
Upselling Microsoft 365 Licenses. It is a deep dive into the differentiators between the various licenses and the benefits that can be derived for your business.
Helping you select the right plan for you and your business.
Connect every employee from the office to the frontline worker. Enhancing productivity and driving innovation.